More Information
Submitted: November 15, 2022 | Approved: November 21, 2022 | Published: November 22, 2022
How to cite this article: Chauhan P, Jaitly T, Agrawal AK. Comparative analysis of mobile forensic proprietary tools: an application in forensic investigation. J Forensic Sci Res. 2022; 6: 077-082.
DOI: 10.29328/journal.jfsr.1001039
Copyright License: © 2022 Chauhan P, et al. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Keywords: Security breach; Mobile forensic; Acquisition; Cumulative evidence; Corroborative evidence and Data extraction
Comparative analysis of mobile forensic proprietary tools: an application in forensic investigation
Parth Chauhan1*, Tamanna Jaitly2 and Animesh Kumar Agrawal1
1School of Digital Forensic Sciences, NICFS, NFSU (Delhi Campus), Ministry of Home Affairs, Govt. of India 2School of Forensic Sciences, NICFS, NFSU (Delhi campus), Ministry of Home Affairs, Govt. of India
*Address for Correspondence: Parth Chauhan, School of Digital Forensic Sciences, NICFS, NFSU (Delhi Campus), Ministry of Home Affairs, Govt. of India Email: [email protected]
The utilization of the Internet and wireless communication reaches its pinnacle from one side of the planet to the other. Marking the rise of criminal activity in recent years sees enormous growth in security breaches and data theft-related cases in mobile phones. To mitigate them, the implementation of security patches, safety fixes, and updates in mobile devices is of high priority for the organization. The need to foster techniques and procedures in the field to be able to extract and precisely dissect digital crime cases, providing valuable tactical data about the investigation. Mobile forensics is a developing branch assisting the investigator in criminal trials and investigations. Acquisition, Collection, and Analysis of mobile phones settle the purpose of recovering cumulative and corroborative evidence. Upgradation and innovation of mobile devices with time imposed a challenge to mobile forensic technology to extract information from such devices. The study aims at extracting comparative and statistical approaches in the analysis of Physical data acquisition utilizing significant versatile mobile criminological proprietary tools. The proposed study also introduces newly developed utility tools along with their characteristic features which help in successful data extraction from mobile devices.
Considering the upward trajectory in urbanization results in a remarkable increase in world population crossing 7.91 billion with augmentation of cyberspace to approximately 4.95 billion as per Digital 2022 Global Overview Report. As the number of users increases day by day, the amount of data generated from mobile devices is at high-security risk. Internet activity focus contributes over 5.31 billion and estimates 67.1% of the total population employs smartphones till Jan 2022. Demographical data manifests 4.62 billion of the total population as dynamic web-based media clients which gauges 58.4% till Jan 2022 [1]. Moderation techniques and strides to these unavoidable dangers paves a way for steady data assurance. Certain Smartphone Industries are looking to mitigate these risks by implementing security patches and updates regularly the Indian smartphone market is pacing upward and reaches 150 Million in 2020 and will increase to 11% with 167 - 168 Million in 2020 with a high prediction of 187 - 190 million market pace in 2022 [1]. This produces a challenge to the forensic investigator to extract useful data from the suspected user’s mobile devices for criminal investigation and trial purposes. Another challenge [2] in mobile forensics is the Boot loop during data extraction which is the device freezing on the startup screen and does not start further, mostly when using a noncompatible mobile forensic tool or the operating system for extraction and acquisition [3]. The scientific process of acquisition, extraction, analysis, and presentation of mobile devices and related evidence in a forensically sound condition is known as Mobile forensics. Mainly [2] mobile forensic tools work on Logical, Physical, and File system acquisition. The application of these acquisition methods mainly depends on the operating system of Mobile devices and the functionality of the tools. The [2] investigator must have an idea about the make & model along with the operating system and its security patch level before choosing any tool for smooth evidence collection for the mobile device. Much research conducted on techniques of data extraction from different mobile devices using open-source and proprietary mobile forensic tools which are now conclusively implemented in forensic labs for extraction purposes. Rusydi Umar, et al. [3] conducted forensic analysis on the WhatsApp application database having .crypt12 encryption using Belkasoft Evidence (Trial version) and WhatsApp Key/DB Extractor in which Whatsapp key/DB Extractor gave better results in extracting text messages while Belkasoft Evidence gave much better results in extracting the media & documents.
Oluwafemi Osho, et al. [4] conducted an evaluation of mobile forensic tools including AccessData FTK, EnCase, MOBILedit Forensic Express and Oxygen Forensic Suite on two mobile devices named HTC Desire 300 with android v4.1.2 and Samsung Galaxy GT-S5300 android v2.3.5 focusing on the recovery of deleted data. They concluded that FTK and EnCase are better in recovery than MOBILedit and Oxygen Forensic Suite. Not only WhatsApp applications, but a previous study [5] was also conducted on forensic analysis of fitness applications in mobile devices using Android Studio and DB browser by manual acquisition. The manual acquisition technique [2] is least considerable due to the fact that the artifact can tamper with while handling the mobile evidence directly. In place of Manual acquisition being considered first [2]. Logical and Physical acquisition is preferable by many forensic laboratories all over the world [6]. The reference study conducted forensic data extraction of five social networking apps using MAGNET AXIOM and MSAB-XRY in three conditions mainly before data deletion, some data deletion from the app, and after uninstallation of the app. The study used logical data acquisition techniques for investigation.
This paper discusses the [7] physical acquisition of an isolated sample mobile device using proprietary tools and the comparative analysis of the recovered artifacts. The study focuses on the practical performance of proprietary tools [8] by testing the artifacts recovery method and its overall features from the acquisition till report generation.
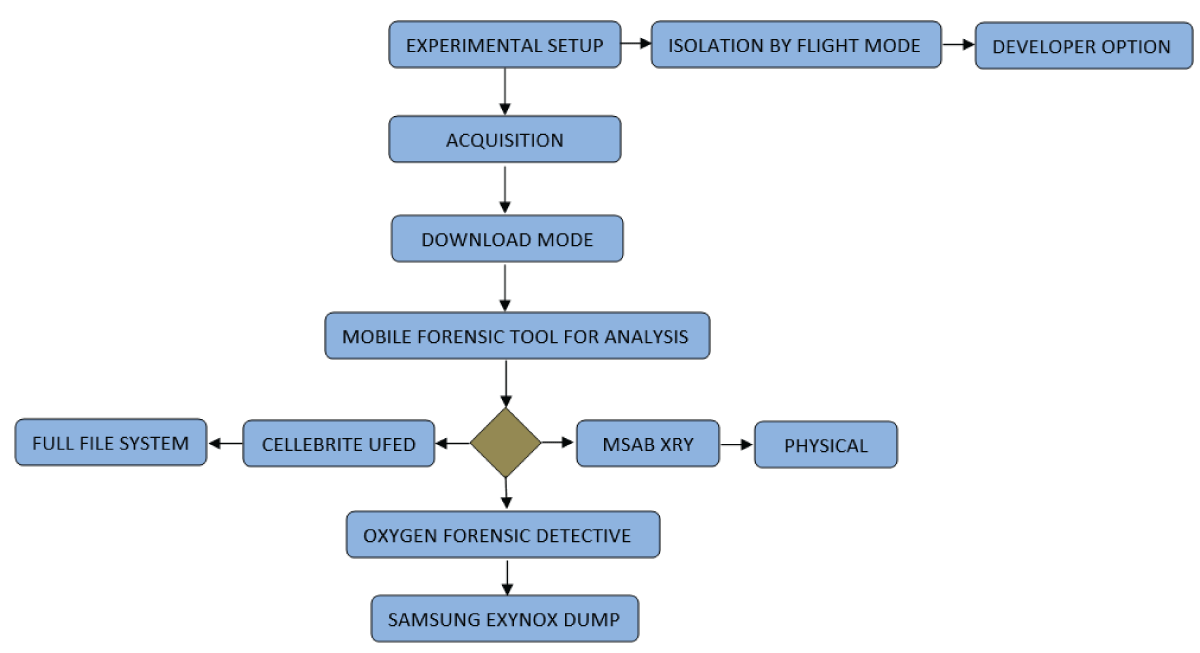
The experiment was partitioned into stages: experimental setup of sample mobile device; acquisition of sample mobile device using three forensic proprietary tools for artifacts gathering and recovery and comparative result generation from the analysis of artifacts recovered from all three forensic tools. As per the current extraction types, generally, extraction is of three types Physical, Logical, and File system. On the other hand, cloud-based extractions can be performed on a separate basis as the data backup resides on cloud storage which has to be exported using token generation and session IDs Image 1.
Image 1: Flow chart explains experimental sections and tools with their physical acquisition techniques.
The sample mobile device was procured (Table 1) and tested in front of laymen with his consent. Note that the SIM was not part of the experimental setup with the intention to narrow down the study. The physical dump is collected by the acquisition of internal and cloud storage only taking into account that SIM would not give much information as compared to the information stored in the social media database, internal storage media, and cloud.
| Table 1: Equipment identification before the examination. | |||
| Device name | Model | Android vesion | security patch level |
| Samsung Galaxy M31 | SM-M315F/DS | 11 | December 1st, 2021 |
Logical extraction may not require physically connecting the mobile device in order to extract the data. Such extraction works on the principle of injection of the third-party application which collects the on-device data. The injection of such third-party applications can either be by connecting the device with OTG or using wireless bandwidth. While in the case of iOS Technology, the older version can be partial jailbreak using the vulnerability engagement in the device.
The system and software information is rechecked online for custom ROM installation [9] by providing an IMEI number at https://www.imei.info/. The compatibility of the Sample mobile device is checked before the acquisition using the [10,11] in-built support of manuals of all three mobile forensic tools [2,12]. The mobile used for testing purposes is checked with the latest android version and security patch level to correctly examine the analytical performance of Forensic tools which helps forensic experts for further analysis in forensic laboratories.
Step one is to isolate the mobile device by enabling Flight mode or Airplane mode [13]. Along with this, enable the developer option and check the stay awake option to prevent the screen from locking [13].
The mobile forensic proprietary tools used for the experimental study are shown in Table 2.
| Table 2: Mobile forensic tools with their version used in an experimental study. | ||
| Tool Used | Version | |
| 1 | MSAB-XRY | 10.0.0 |
| 2 | Cellebrite UFED4PC | 7.50.0.137 |
| 3 | Oxygen Forensic Detective | 13.6.0.47 |
Staging towards the acquisition part after completing the experimental setup of the sample device, the mobile device is now connected to the particular tool at a time for the data collection using physical acquisition [2,14]. To complete the step of acquisition, a mobile device is necessary to put in download mode (Image 2).
Image 2: Download mode enabled in Sample mobile device.
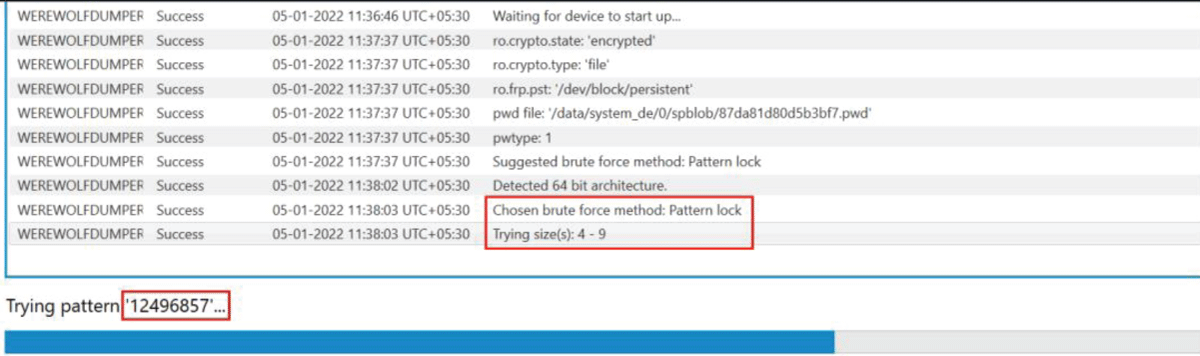
The mobile phone is made pattern locked with 8 keys in pattern as “729513486” So to check whether these tools were able to bypass or crack the pattern lock and the type of technique they adopt [13] Image 3.
Image 3: Brute Forcing of pattern lock in Samsung M31 using MSAB-XRY.
A special booting mode specifically made by Samsung for certified repair technicians to get the root access privilege and debug the system easily for easy maintenance, software, and firmware updates along with recovery of data [13,15,16] Images 4-6.
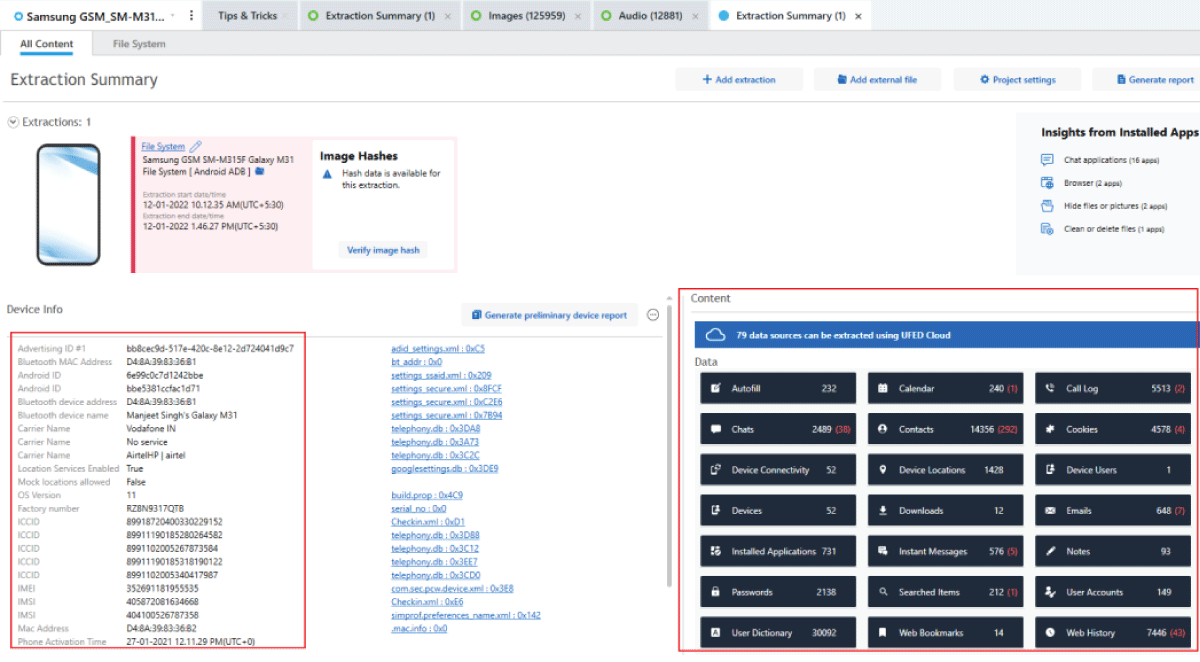
Image 4: Cellebrite UFED interface after extraction.
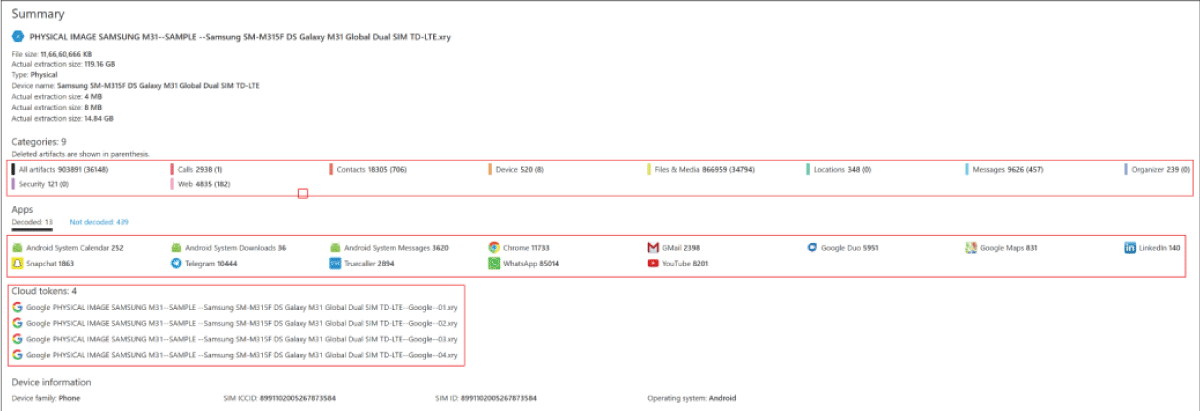
Image 5: MSAB XRY interface after extraction.
Image 6: Oxygen Forensic Detective interface after extraction.
The objective of this study is fulfilled by examining the working performance of mobile forensic proprietary tools using Physical acquisition [17-20] with a major focus on the recovery of deleted artifacts. The artifacts collected from the examination using different tools are shown in Tables 3,4.
| Table 3: Total artifacts retrieved from Samsung Galaxy M31 SM-M315F/DS. | |||
| Category | Tools used | ||
| Cellebrite UFED | MSAB-XRY | Oxygen Forensic Detective | |
| Total artifacts | 553455 | 940039 | 1176939 |
| Table 4: Categorization of artifacts retrieved from Samsung Galaxy M31 SM-M315F/DS. | |||
| Data category | Tools used | ||
| cellebrite UFED | MSAB XRY | Oxygen Forensic Detective | |
| call logs | 5513(2) | 2938(1) | 14364 |
| contacts | 14356(292) | 18305(706) | 9364 |
| device | 731(0) | 520(8) | Not Categorized |
| files&media | 407551(12682) | 866959(34794) | 571339 |
| locations | 1428(0) | 348(0) | Not Categorized |
| messages | 3713(50) | 9626(457) | 581574 |
| calender | 240(1) | 239(0) | 514 |
| user accounts | 149 | 116 | 133 |
| web data | 7460(43) | 4835(182) | 2080 |
| Note: Deleted Artificats are shows in parenthesis | |||
For dead devices, chipset-based extraction is performed in order to get the physical dump of data. Along with this method, the device was turned into suitable mode by pressing certain keys which make the tool perform the exploit. However, the chances of getting more amount of deleted data are higher in the case of extraction of the rooted device as compared to the non-rooted one. In order to get the deleted data by physical extraction, the device was made into flashed and made into partial root mode which is called download mode or Emergency Download mode (EDL).
The study highlighted the data extraction using Download mode [13,15,16] which is specifically built for technical support and maintenance in Samsung smartphones. Other factors were also considered for the proper analysis of tools as shown in Table 5.
| Table 5: Comparison of tools. | |||
| Factors | Tools used | ||
| Cellebrite UFED | MSAB-XRY | Oxygen Forensic Detective | |
| Interface usability | |||
| Device compatibility | |||
| Log Report generation | × | × | |
| Hashing of report | |||
One of the reasons for considering MSAB XRY over other mobile forensic tools mentioned above is the generation of log reports to examine the errors while performing acquisition. On the other hand [11]. Oxygen forensic detective summarizes artifacts in a much better way than the above tools by filtering the data according to the type of file and application separately [10]. UFED and XRY are more efficient in data and meta-carving as compared to Oxygen Forensic Detective.
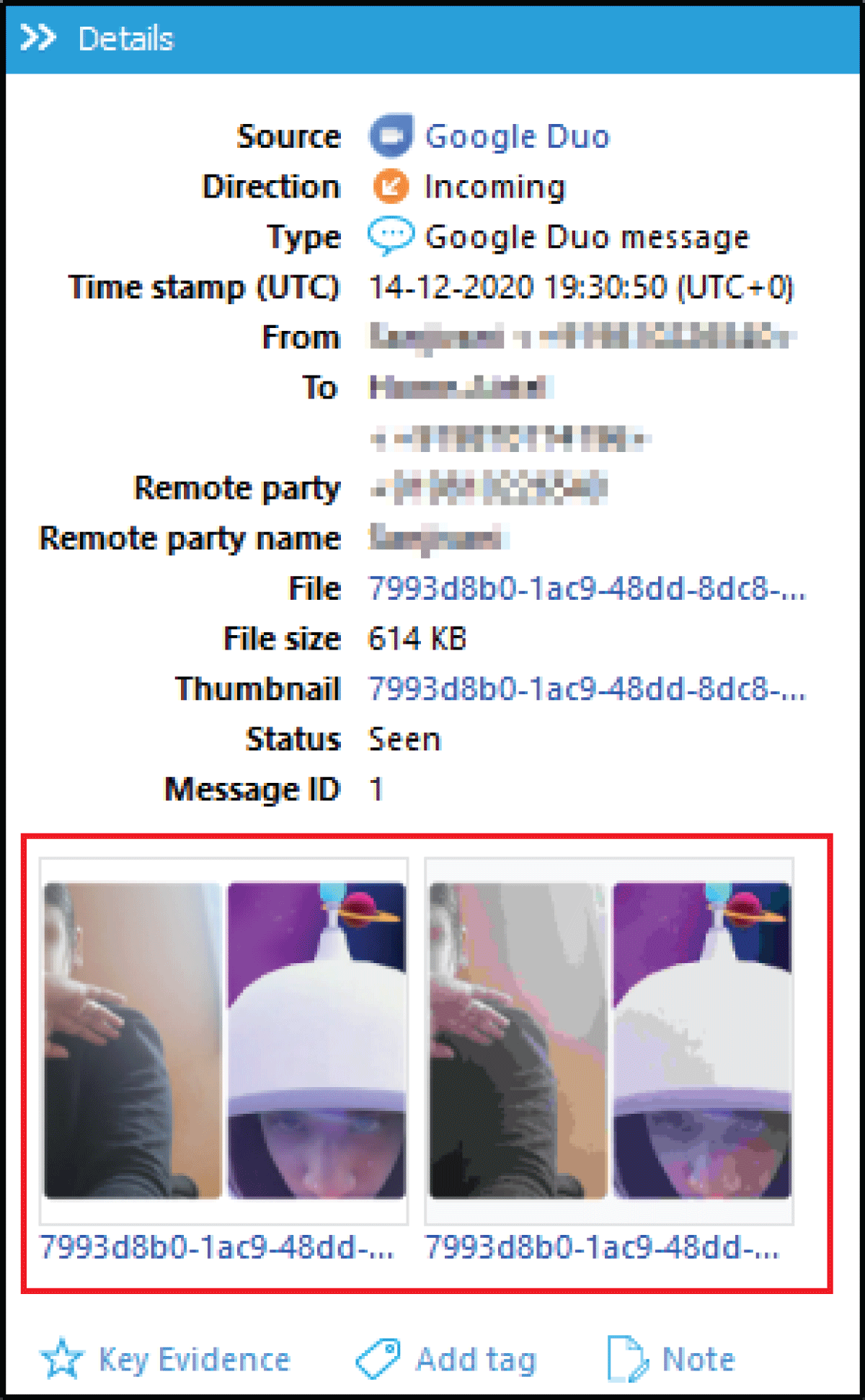
Analyzing social media artifacts, Oxygen Forensic Detective finds a vast range of artifacts especially for Whatsapp and Google Duo by extracting the on-call snapshots as compared to other tools as shown in Image 6. The above study was found to be helpful for forensic investigators in mitigating the challenge of unlocking Samsung smartphones, efficient analysis & report generation [8] Image 7.
Image 7: On-call snapshot retrieved by Oxygen Forensic Detective.
Above mentioned tools, Cellebrite UFED, MSAB XRY and Oxygen Forensic Detective were found to give the best results in different domains of artifact retrieval. The functionality of these proprietary tools is much better in all aspects as compared with open-source tools. In the advancement of Mobile Forensics, the tools need to be updated with the latest Mobile device modules and technology to recover deleted artifacts. Extracting the artifacts from the latest android and security patch level will always be a challenge to forensic experts. The extraction of social messaging application data is a challenging task in view of the probability of finding critical evidence is more as compared to other artifacts. Capturing the token and in order to live capturing of cloud-based application data is another challenging task for law enforcement agencies as well as proprietary tool manufacturers. The research in the developing field of forensic science cannot be compromised by the upgradation of smartphones.
- Simon K, Pte K. Ltd. https://datareportal.com/reports/digital-2022-global-overview-report
- Lahesoo P, Mäses S. Forensic Traces of Messaging Applications on Android and iOS Mobile phones.
- Umar R, Riadi I, Zamroni GM. Mobile forensic tools evaluation for digital crime investigation. Int J Adv Sci Eng Inf Technol. 2018; 8(3): 949.
- Osho O, Ohida SO. Comparative evaluation of mobile forensic tools. IJ Inf. Technol. Comput. Sci. 2016; 1:74-83.
- Sinha R, Sihag V, Choudhary G, Vardhan M, Singh P. Forensic Analysis of Fitness Applications on Android. In the International Symposium on Mobile Internet Security 2021; 222:235.
- Aljahdali A, Alsaidi N, Alsafri M, Alsulami A, Almutairi, T. Mobile device forensics. Romanian Journal of Information Technology and Automatic Control. 2021; 31(3): 81-96.
- Eriş FG, Akbal E. Forensic Analysis of Popular Social Media Applications on Android Smartphones. Balkan Journal of Electrical and Computer Engineering. 2021; 9(4):386-397.
- Dasgupta RK. Mobile forensic: Investigation of dead or damaged smartphone-An overview, tools and technique challenges from law enforcement perspective. Research gate Journal. 2021. https://www.researchgate.net/profile/Rhythm-Dasgupta/publication/340939977_Mobile_Forensic_Investigation_of_Dead_or_Damage_Smart_Phone_-An_Overview_Tools_Technique_Challenges_from_Law_Enforcement_Perspective/links/5ea68b62299bf11256128683/Mobile-Forensic-Investigation-of-Dead-or-Damage-Smart-Phone-An-Overview-Tools-Technique-Challenges-from-Law-Enforcement-Perspective.pdf
- Agrawal AK, Sharma A, Sinha SR, Khatri P. Forensic of an unrooted mobile device. International Journal of Electronic Security and Digital Forensics. 2020; 12(1):118-137.
- Release notes (September 2019). UFED 4PC, UFED Touch 2, and UFED InField v7.23 https://cf-media.cellebrite.com/wp-content/uploads/2019/09/ReleaseNotes_7.23.pdf
- Press Release (December 2021). Oxygen Forensics Closes the year with Major upgrades in extraction capabilities, VPN support, Data analysis, and more. https://www.oxygen-forensic.com/uploads/press_kit/OFDv142ReleaseNotes.pdf
- Hazra S, Mateti P. Challenges in android forensics. In International Symposium on Security in Computing and Communication. 2017; 286-299. Springer, Singapore.
- Joshua J, Zach Lanier D, Mulliner C, Fora O, Ridley SA, Android’s GW. Hacker Handbook, John Wiley& Sons; https://books.google.co.in/books?id=2qo6AwAAQBAJ&printsec=frontcover&source=gbs_ge_summary_r&cad=0#v=onepage&q&f=false 2014.
- Gaikar V. Article by Tricks Machine on How to root samsung galaxy S3. 2012. https://www.tricksmachine.com/2012/07/how-to-root-samsung-galaxy-s3.html
- Kong J. Data extraction on mtk-based android mobile phone forensics. Journal of Digital Forensics, Security and Law2015; 10(4): 3.
- Alendal G, Dyrkolbotn GO, Axelsson S. Forensics acquisition—Analysis and circumvention of samsung secure boot enforced common criteria mode. Digital Investigation. 2018; 24: S60-S67.
- Tajuddin TB, Abd Manaf A. Forensic investigation and analysis on digital evidence discovery through physical acquisition on the smartphone. In 2015 World Congress on Internet Security (WorldCIS). IEEE. 132-138.
- Sathe SC, Dongre NM. Data acquisition techniques in mobile forensics. In 2018 2nd international conference on inventive systems and control (icisc). IEEE. 2018; 280-286.
- Ayers R. Smart Phone Tool Specification, computer forensic tool testing. 2010. https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=905497,www.cftt.nist.gov
- Osho O, Ohida SO. Comparative evaluation of mobile forensic tools. IJ Inf. Technol. Comput. Sci, 2016; 1:74-83.